-
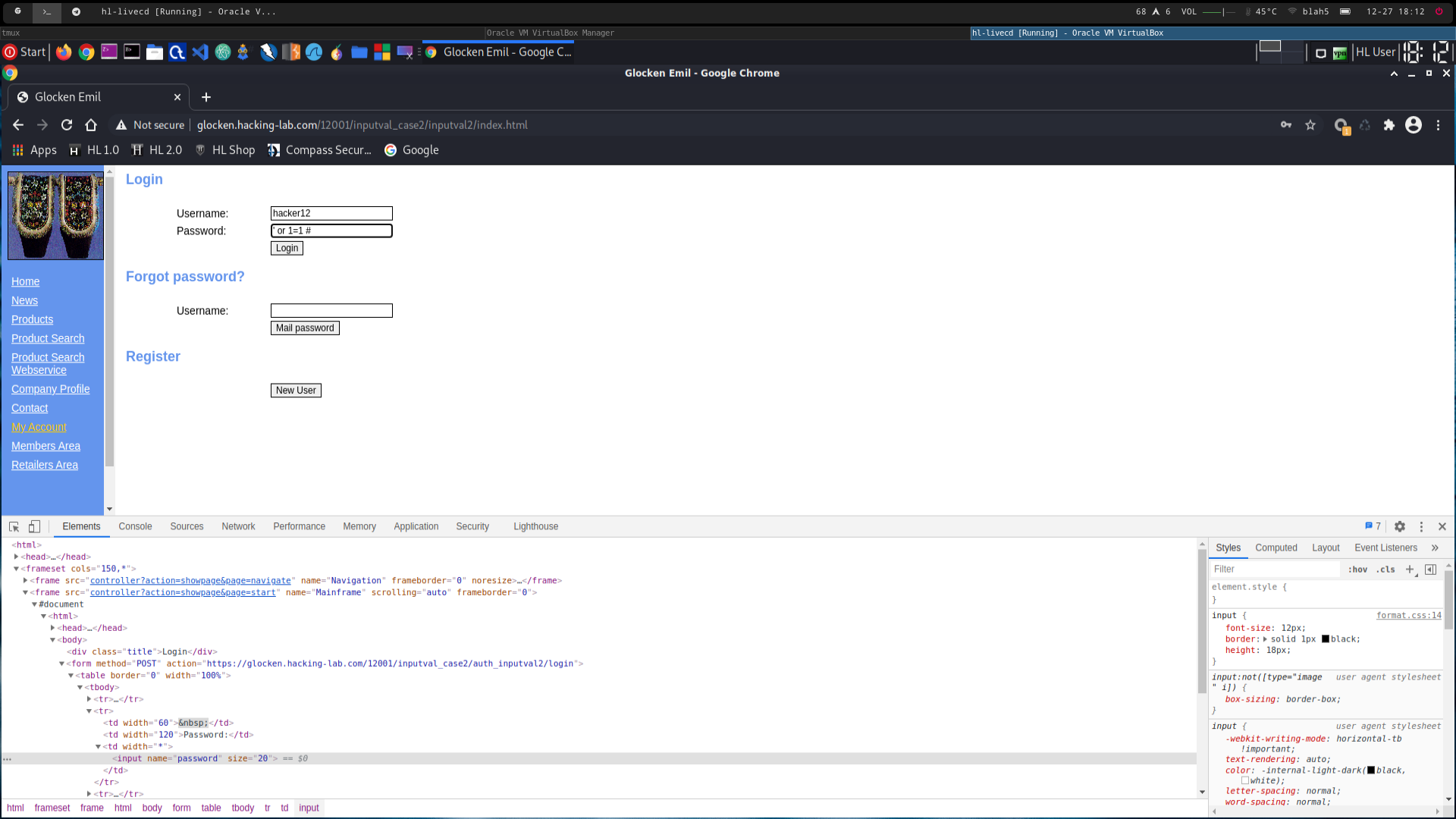
sql injection possible (entered string is directly put into sql statement, this means the hacker can forge whatever he wants to modify the request, like ending the password string, or'ing it with 1=1 (true), and commenting out the rest of the line)
-
enter
' or 1=1 # as password (see 2310_1.png, password input type changed to show the password)
-
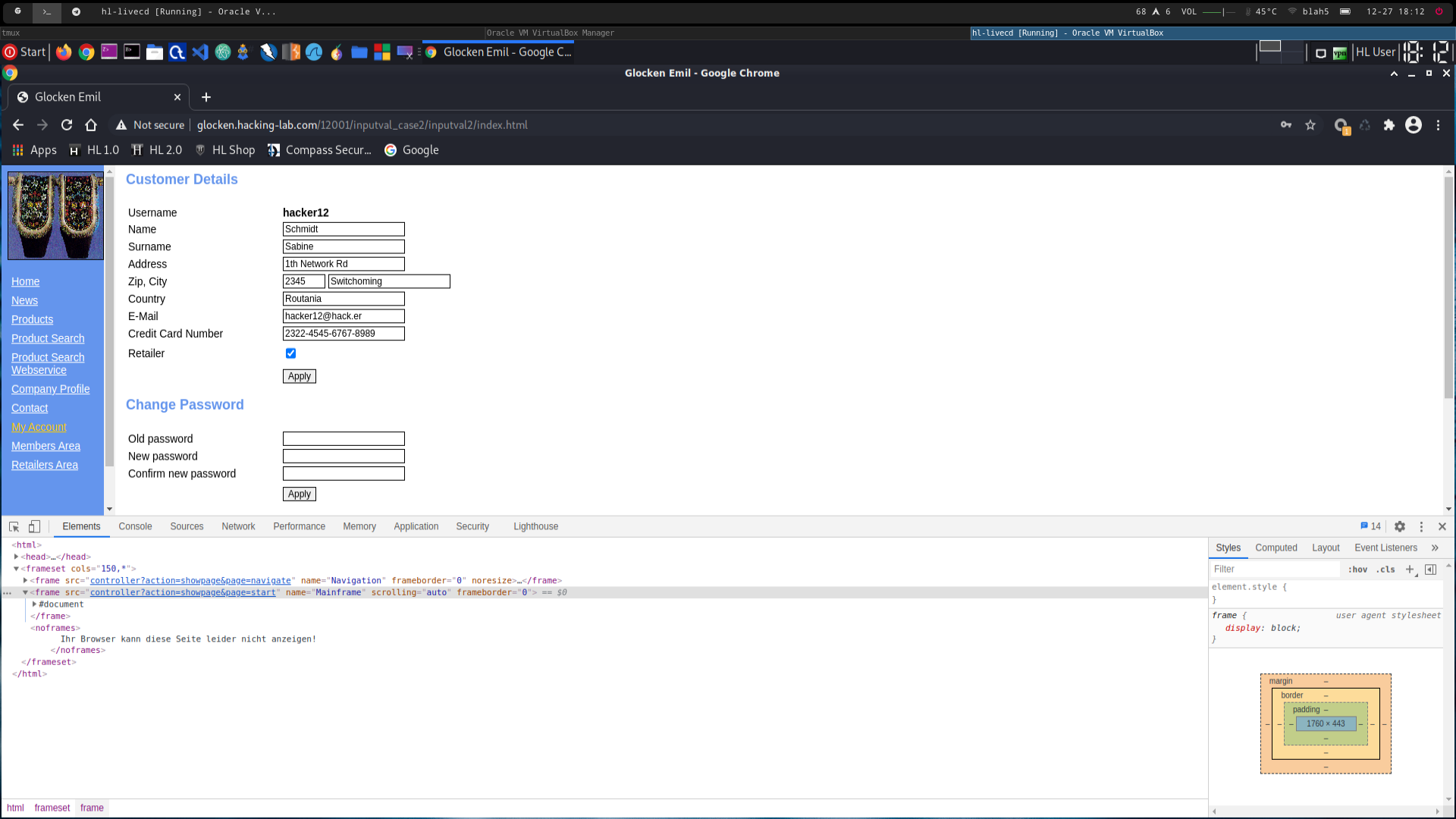
the access is granted (see 2310_2.png)
-
escape (sanitize) the user input
-
use prepared statements (the user input is treated as a variable, so
' or 1=1 # is treated literally and the password will get compared with this string)


