-
xml injection possible (kind of. As the injection is happening on client side in JavaScript, the request could get replaced entirely (but this would not use the requested vulnerability of the task))
-
examine the source code of the page -> the xml is constructed in javascript (see 2600c_1.png)
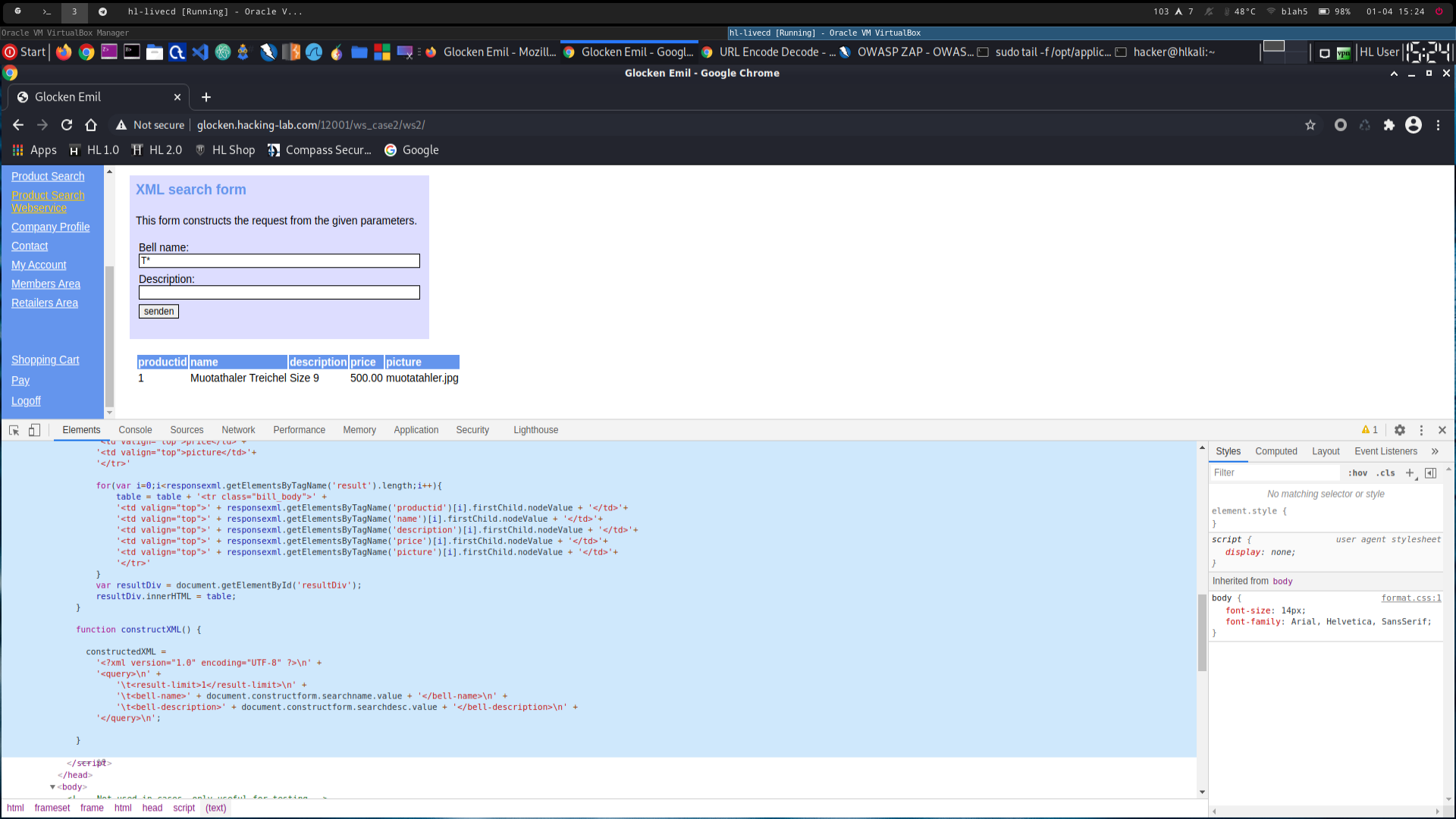
-
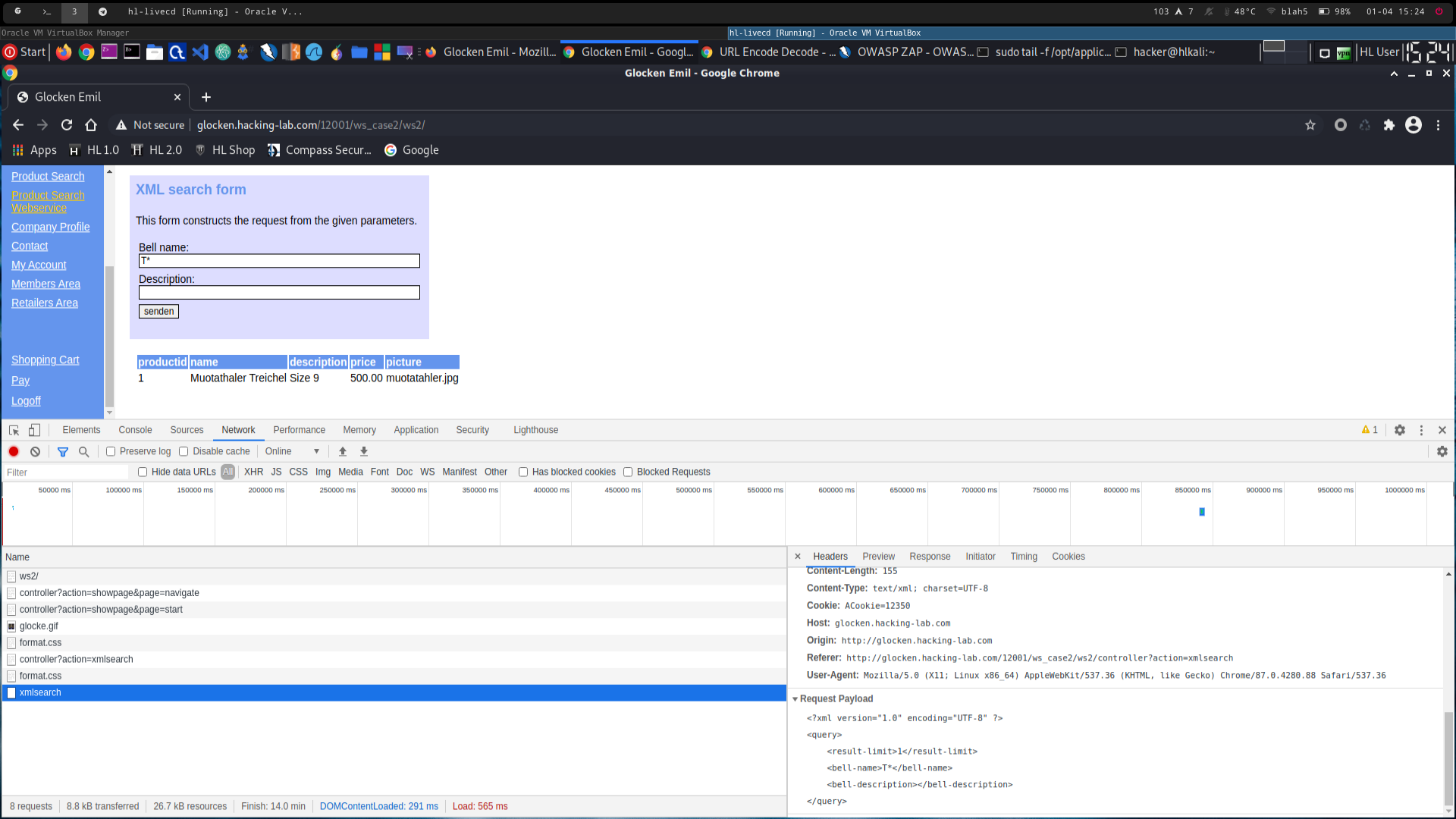
make a normal request with
T* as bell name and validate that the request is made as expected (see 2600c_2.png)
-
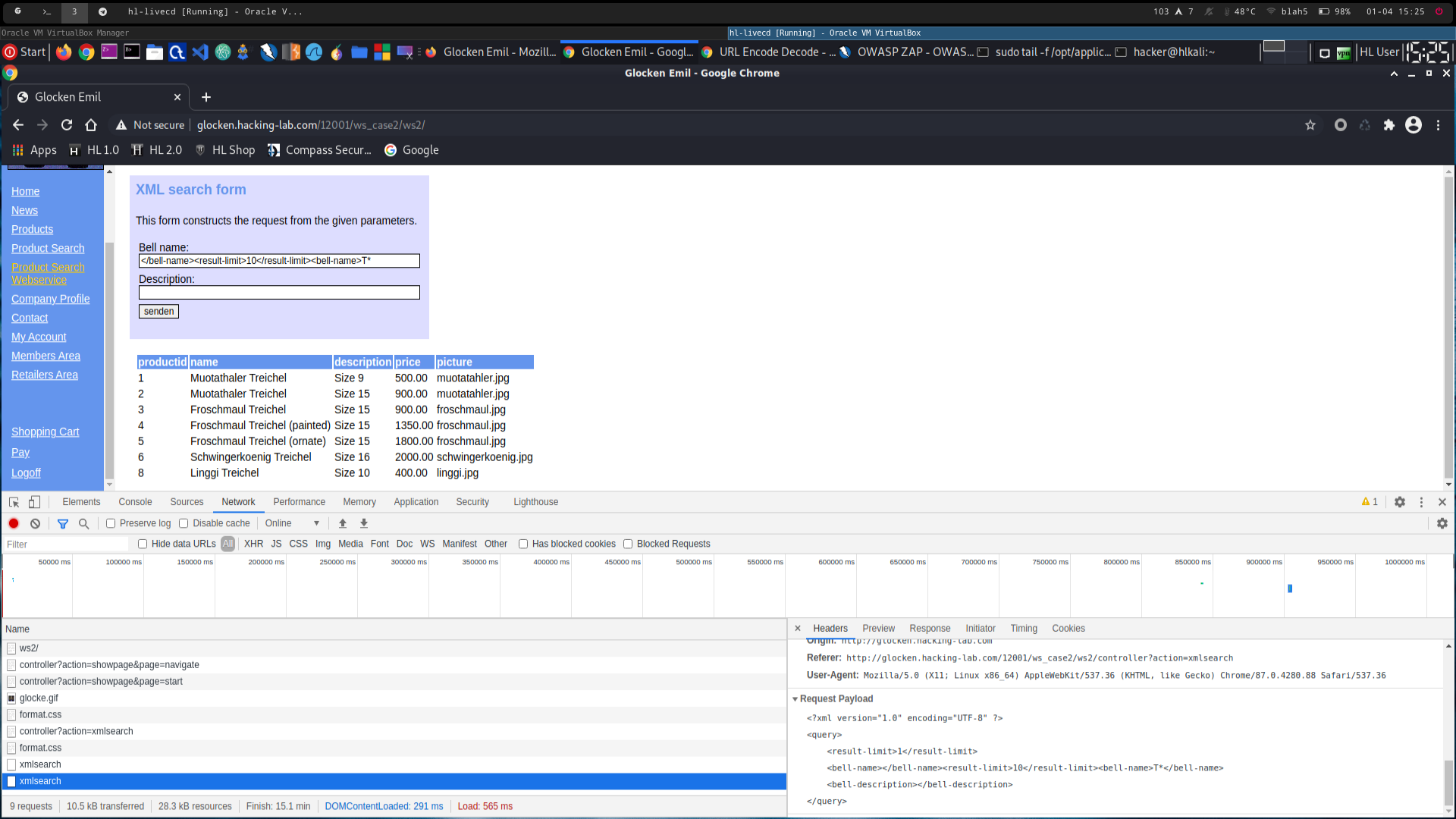
make modified request with
</bell-name><result-limit>10</result-limit><bell-name>T* as bell name (see 2600c_3.png)
-
sanitize user input (of no actual use, as it can get bypassed in this scenario, by forging the entire request manually, as the user input is only part of the request)
-
only allow fields that should be able to get changed (e.g.
result-limit only if you want to allow the user to retrieve more than one item at once)
-
do not allow xml requests at all -> only the form data as request, properly sanitize on server side



