-
clickjack attack possible
-
iframe, overlapped with blank rectangles to hide the rest of the original page
-
transparent iframe overlapping the fake page, which triggers the user to click on it, but ultimately clicking on the transparent iframe
-
prepare page that uses aforementioned features (see 2670_0.png)

-
get victim to use this page
-
pictures:
-
(2670_0.png -> the clickjack is kind of broken. The lower part is shown as soon as the user "leaves" the upper part with the mouse. If the victim never actually orders something, the newly present "Jetzt bestätigen" is doing nothing - not even hidden)

-
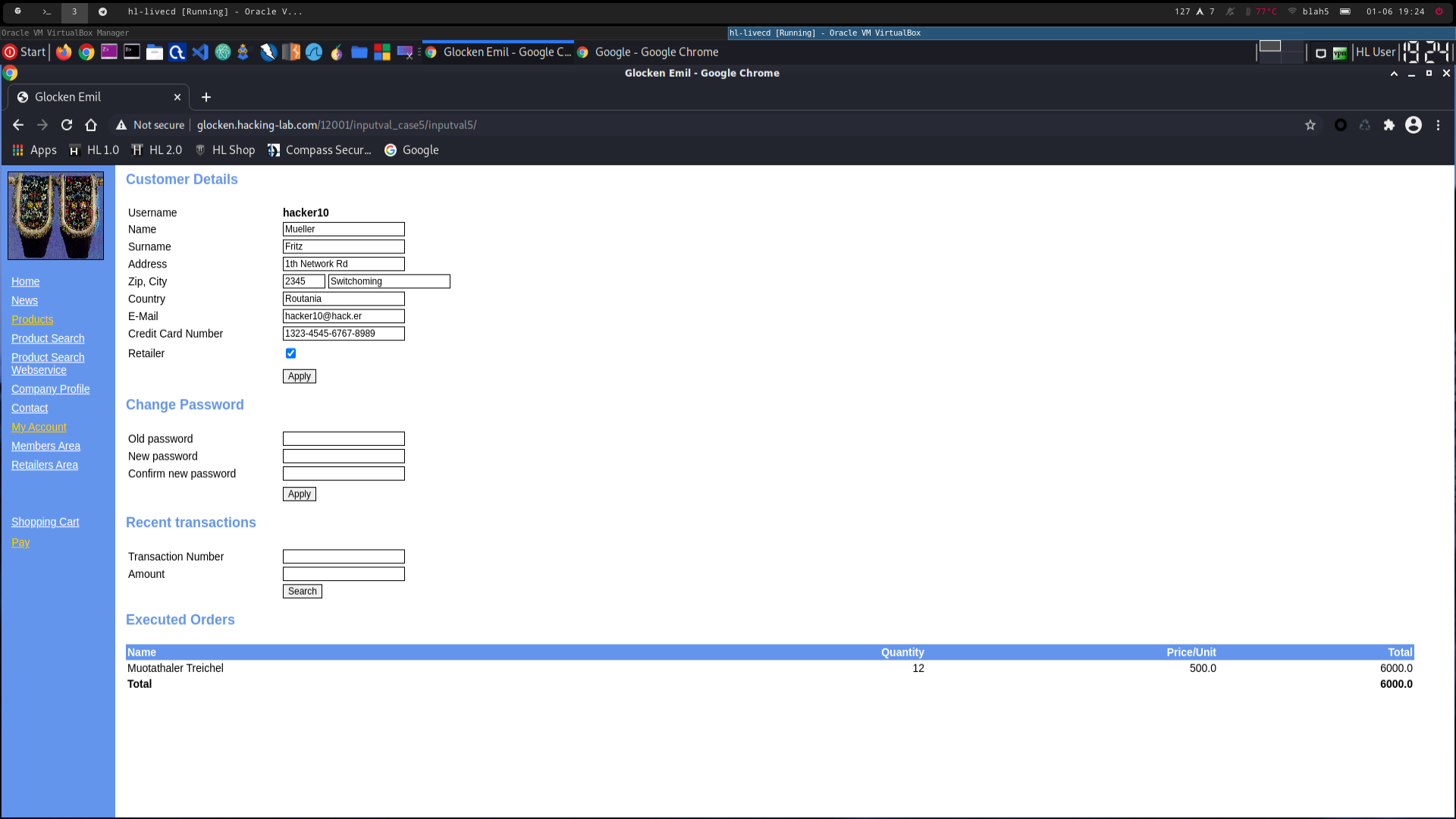
2670_1.png -> victim used shop normally
-
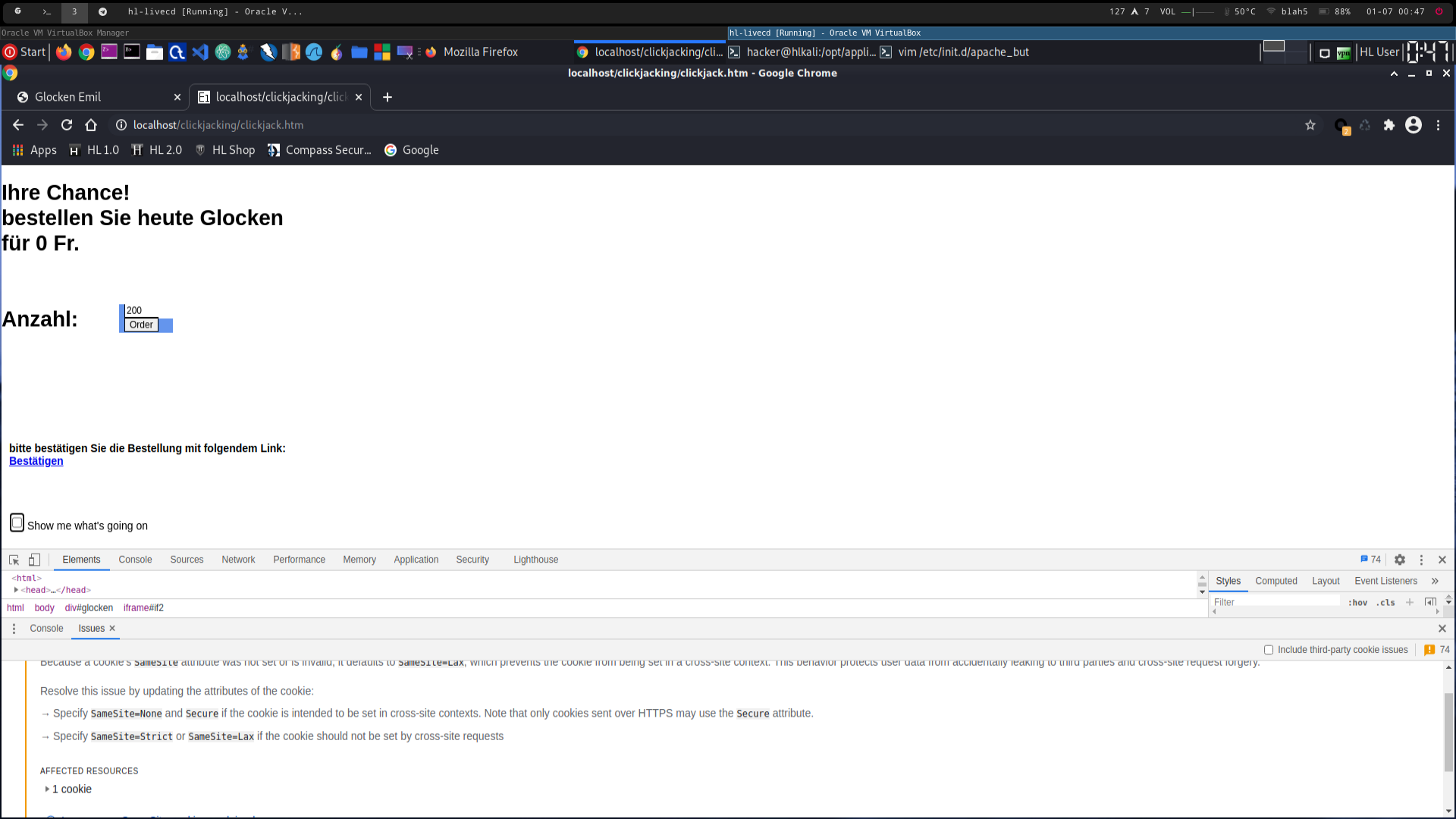
2670_2.png -> victim opens hackers page (chrome already shows - in developer console - that it is not applying the cookies in the cross site context)
-
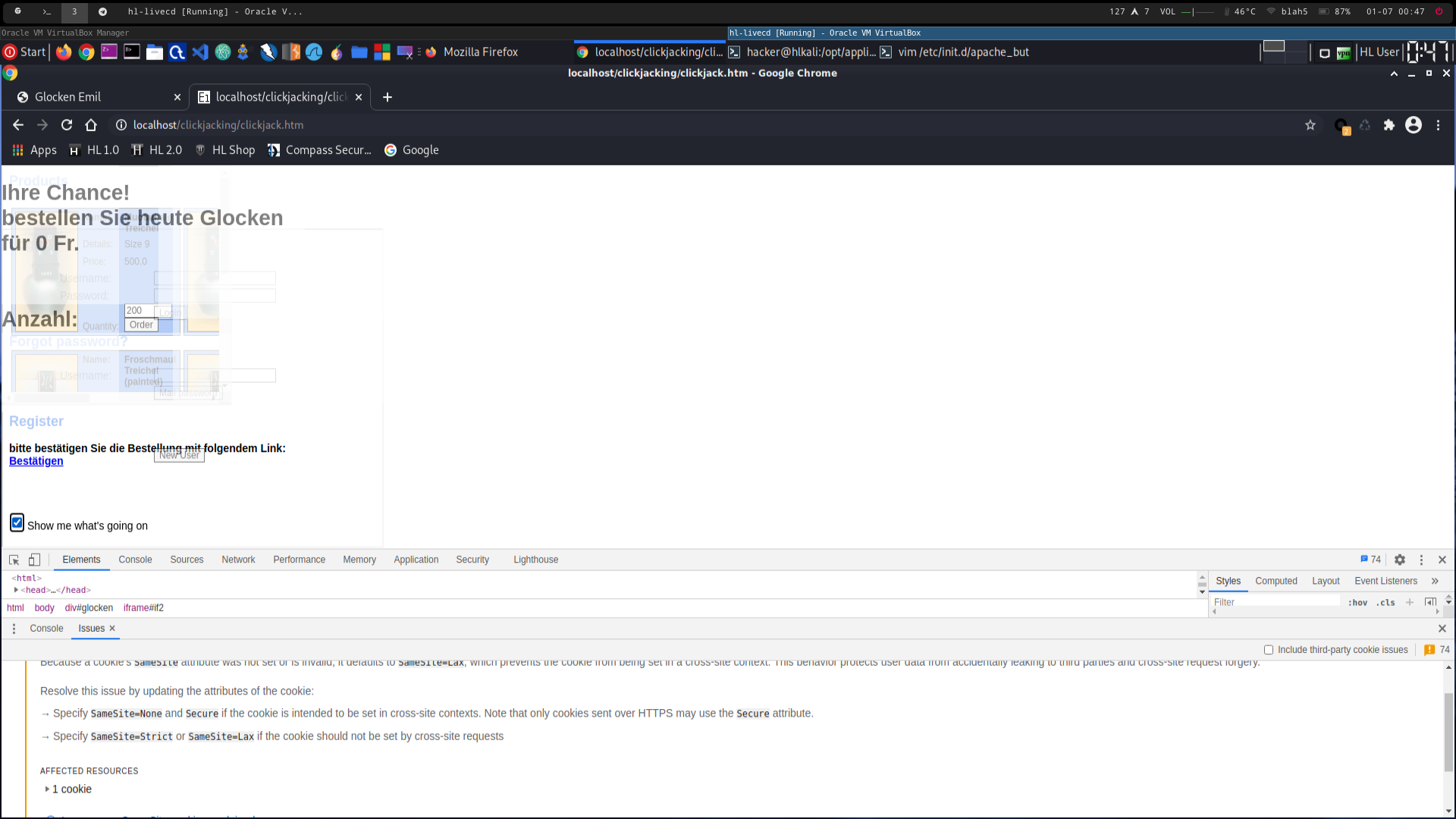
2670_3.png -> victim would click on "Jetzt bestätigen" (as chrome is not applying the cookies, the "pay" iframe shows the login page)
-
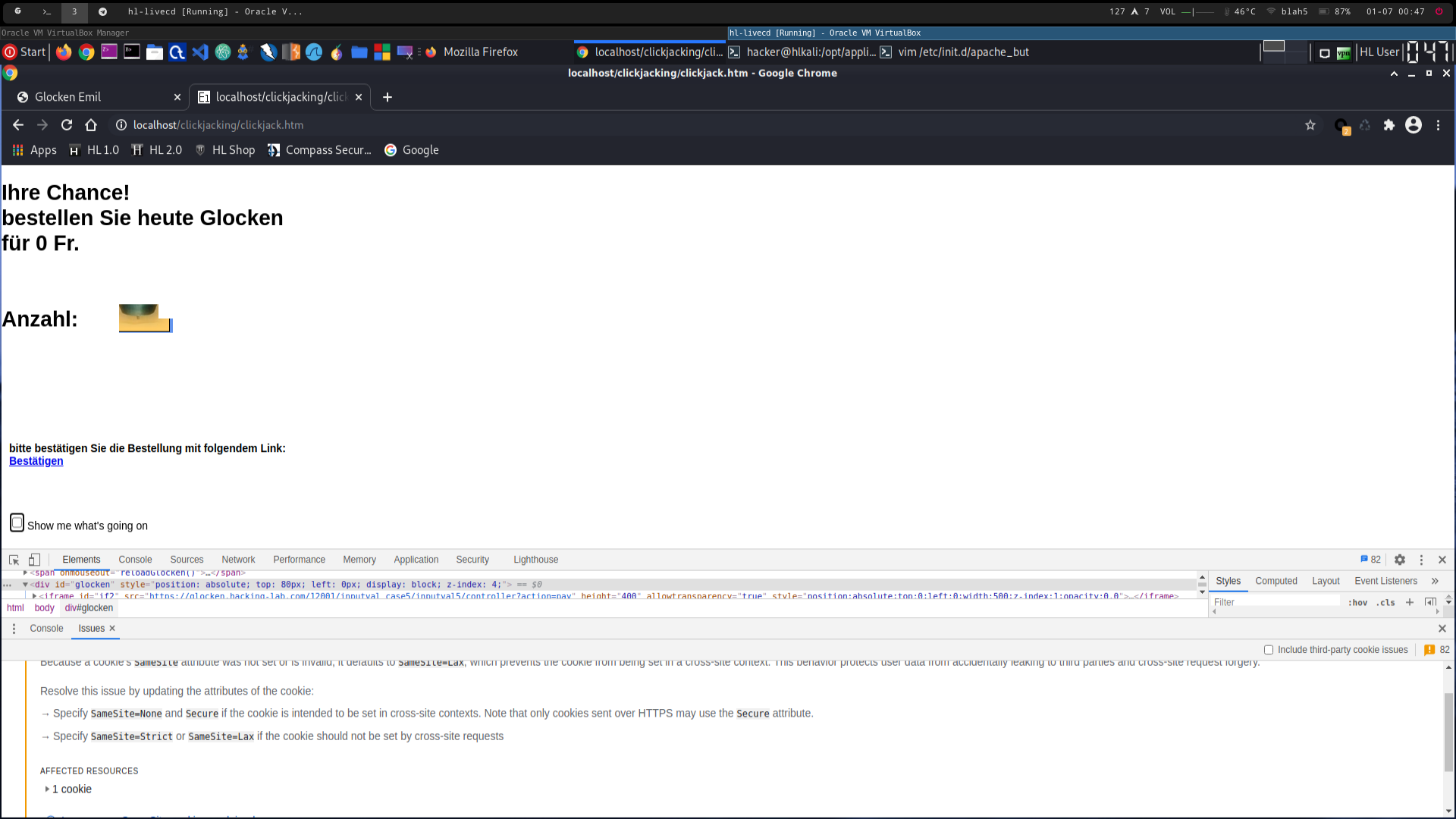
(2670_4.png -> the used iframes are scrollable, so the victim may see the clickjack attack by scrolling)
-
(2670_5.png -> chrome highlights that an iframe from another origin is used, as apposed to the normal message seen in 2670_6.png)


-
2670_7.png -> firefox counter part to 2670_3.png. The user is able to click on the iframe that overlaps the "Jetzt bestätigen" to pay per bill
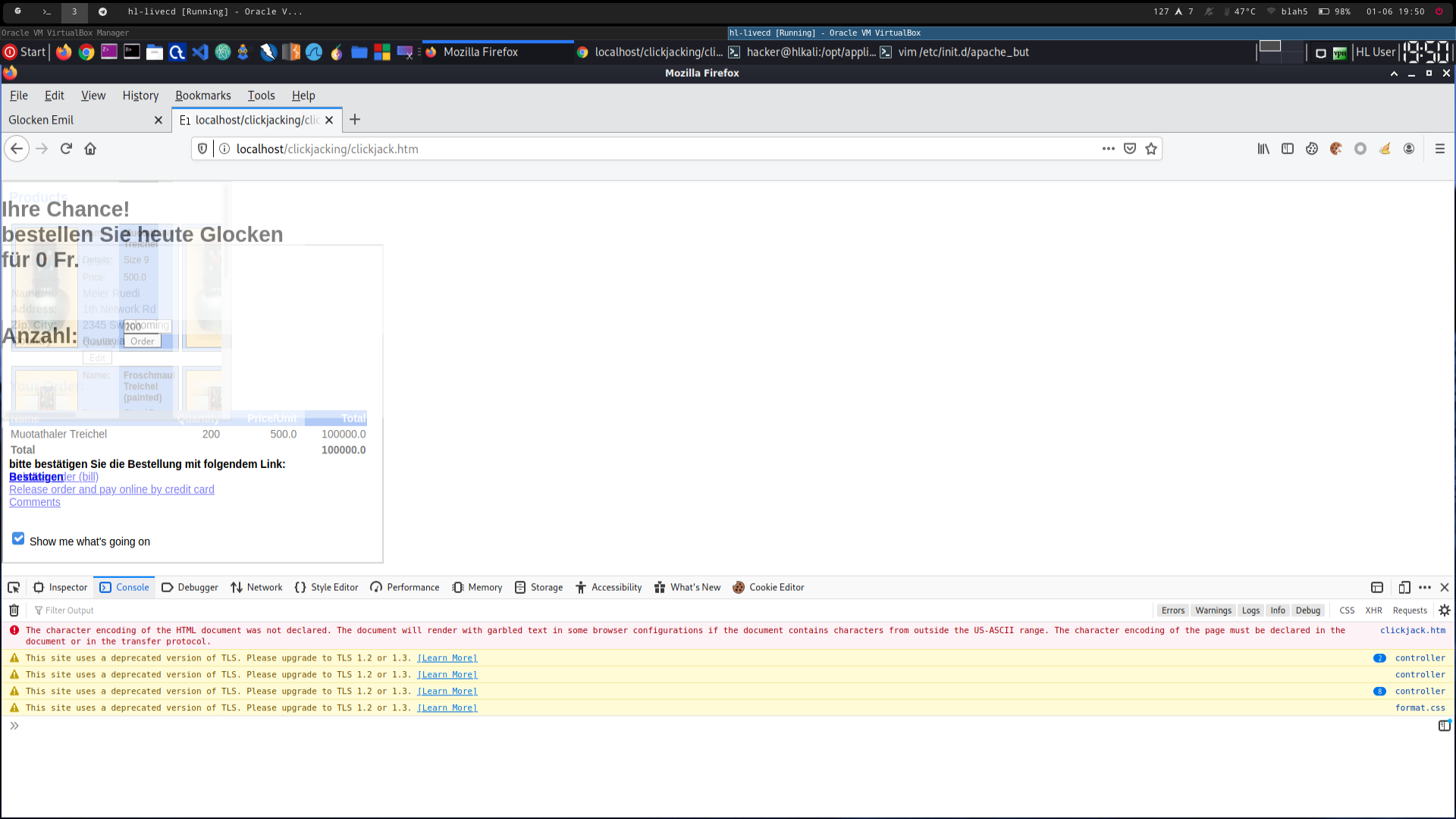
-
client side:
-
(use chrome) (as shown above, chrome by default blocks cross site cookies, which negates the proposed use case, but clickjacking itself is still possible)
-
use ClearClick (a feature of NoScript)
-
webpage side:
-
Content-Security-Policy: frame-ancestors 'none'
-
'none' -> deny embedding of this page - if the used browser respects this header
-
'self' -> allow embedding from same origin (the one applicable for the GlockenEmil shop)
-
example.com hacking-lab.com -> embedding by specific hosts
-
framekillers -> scripts that hide the page if displayed in iframes (unreliable)









