
192.168.200.203/32 (it's only one machine, but as the range is asked, the cidr notation of a single host is used)
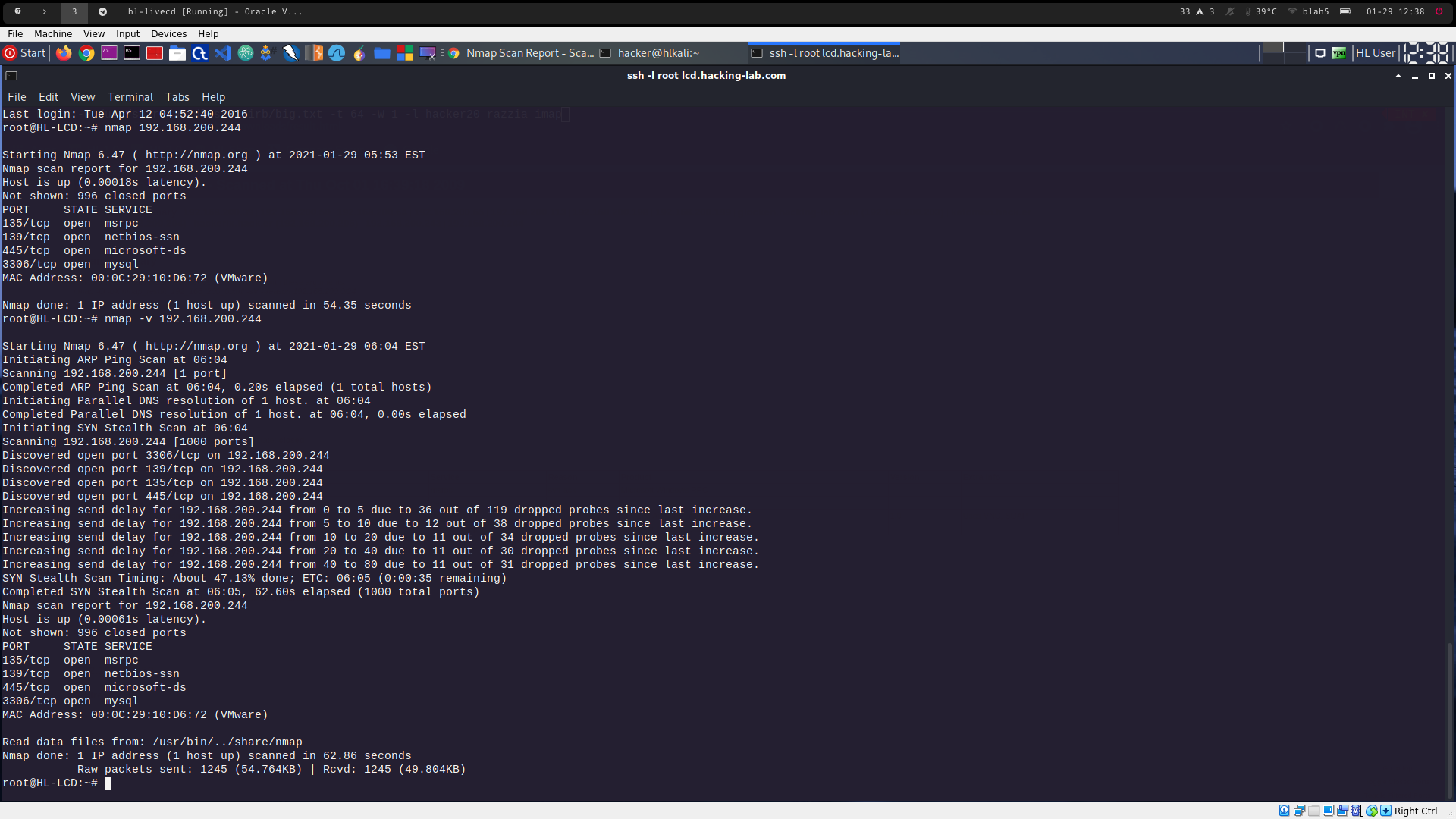
Nmap scan report for conficker.hacking-lab.com (192.168.200.244) Host is up (0.11s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds 3306/tcp open mysql MySQL 5.0.45-community-nt Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Nmap scan report for iloveshells.hacking-lab.com (192.168.200.143) Host is up (0.10s latency). Not shown: 978 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.3.4 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0) 23/tcp open telnet Linux telnetd 25/tcp open smtp Postfix smtpd 53/tcp open domain (generic dns response: NOTIMP) 80/tcp open http Apache httpd 2.2.8 (DAV/2) 111/tcp open rpcbind 2 (RPC #100000) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 512/tcp open exec netkit-rsh rexecd 513/tcp open login? 514/tcp open tcpwrapped 1099/tcp open java-rmi GNU Classpath grmiregistry 1524/tcp open ingreslock? 2049/tcp open nfs 2-4 (RPC #100003) 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5 5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7 5900/tcp open vnc VNC (protocol 3.3) 6000/tcp open X11 (access denied) 6667/tcp open irc UnrealIRCd 8009/tcp open ajp13? 8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1 2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service : ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port53-TCP:V=7.91%I=7%D=1/30%Time=60159A06%P=x86_64-pc-linux-gnu%r(DNSS SF:tatusRequestTCP,E,"\0\x0c\0\0\x90\x04\0\0\0\0\0\0\0\0"); ==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)============== SF-Port1524-TCP:V=7.91%I=7%D=1/30%Time=60159A01%P=x86_64-pc-linux-gnu%r(Ge SF:nericLines,64,"root@iloveshells:/#\x20root@iloveshells:/#\x20root@ilove SF:shells:/#\x20root@iloveshells:/#\x20root@iloveshells:/#\x20")%r(GetRequ SF:est,14,"root@iloveshells:/#\x20")%r(HTTPOptions,14,"root@iloveshells:/# SF:\x20")%r(RTSPRequest,14,"root@iloveshells:/#\x20")%r(RPCCheck,14,"root@ SF:iloveshells:/#\x20")%r(DNSVersionBindReqTCP,14,"root@iloveshells:/#\x20 SF:")%r(DNSStatusRequestTCP,14,"root@iloveshells:/#\x20")%r(Help,14,"root@ SF:iloveshells:/#\x20")%r(SSLSessionReq,14,"root@iloveshells:/#\x20")%r(Te SF:rminalServerCookie,14,"root@iloveshells:/#\x20")%r(TLSSessionReq,75,"ro SF:ot@iloveshells:/#\x20\x1b\[H\x1b\[Jbash:\x20eUrandom1random2random3rand SF:om4/:\x20No\x20such\x20file\x20or\x20directory\n\x1b\[H\x1b\[Jroot@ilov SF:eshells:/#\x20")%r(Kerberos,14,"root@iloveshells:/#\x20")%r(SMBProgNeg, SF:14,"root@iloveshells:/#\x20")%r(X11Probe,14,"root@iloveshells:/#\x20")% SF:r(FourOhFourRequest,14,"root@iloveshells:/#\x20")%r(LPDString,49,"root@ SF:iloveshells:/#\x20bash:\x20default:\x20command\x20not\x20found\nroot@il SF:oveshells:/#\x20")%r(LDAPSearchReq,5C,"root@iloveshells:/#\x20bash:\x20 SF:chimBH:\x20command\x20not\x20found\nroot@iloveshells:/#\x20root@ilovesh SF:ells:/#\x20")%r(LDAPBindReq,14,"root@iloveshells:/#\x20")%r(SIPOptions, SF:35,"root@iloveshells:/#\x20bash:\x20OPTIONS:\x20command\x20not\x20found SF:\n")%r(LANDesk-RC,14,"root@iloveshells:/#\x20")%r(TerminalServer,14,"ro SF:ot@iloveshells:/#\x20")%r(NCP,14,"root@iloveshells:/#\x20")%r(NotesRPC, SF:4D,"root@iloveshells:/#\x20bash:\x20:@/:\x20No\x20such\x20file\x20or\x2 SF:0directory\nroot@iloveshells:/#\x20")%r(JavaRMI,14,"root@iloveshells:/# SF:\x20")%r(WMSRequest,14,"root@iloveshells:/#\x20")%r(oracle-tns,14,"root SF:@iloveshells:/#\x20")%r(ms-sql-s,5B,"root@iloveshells:/#\x20\x1b\[H\x1b SF:\[Jbash:\x20UMSSQLServerH:\x20command\x20not\x20found\n\x1b\[H\x1b\[Jro SF:ot@iloveshells:/#\x20")%r(afp,14,"root@iloveshells:/#\x20")%r(giop,14," SF:root@iloveshells:/#\x20"); Service Info: Hosts: metasploitable.localdomain, 127.0.0.1, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel