-
password hash is saved in the file and can get cracked
-
the password hash is only 40 bit long
-
same password is used for open and edit access
-
use office2john.py to get the password hash from the file
-
Retrieve office2john.py, as it is not part of the default distribution present in Kali:
curl -O https://raw.githubusercontent.com/openwall/john/bleeding-jumbo/run/office2john.py
-
python office2john.py Geheimdoc.xls > hash.txt
-
use john to crack the hash:
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
-
to show the hash again, after execution:
john --show hash.txt (see 5021_1.png)
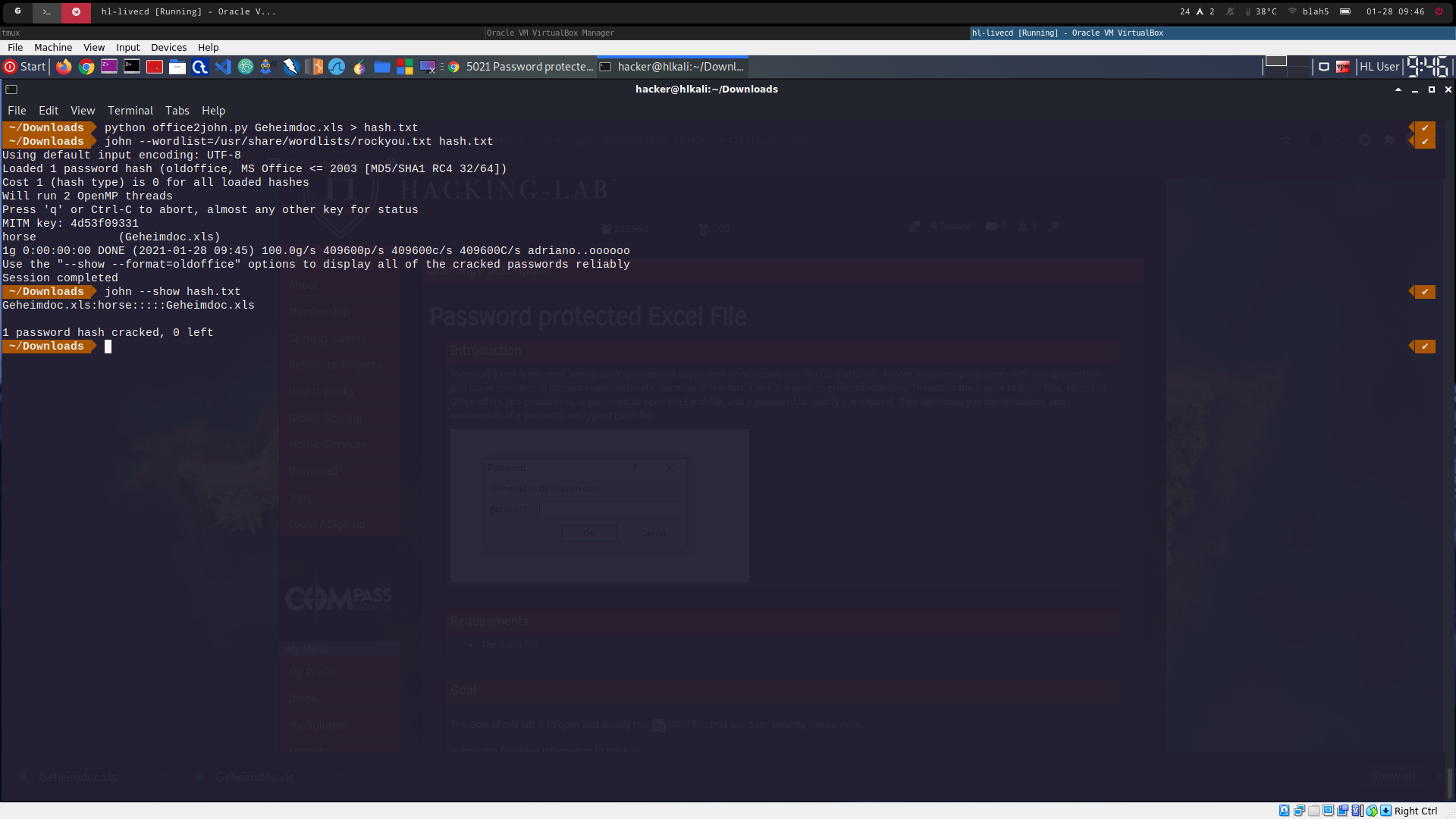
-
the password is: horse (or at least the password shares the same hash with
horse)
-
see 5021_2.png for opened and modified file
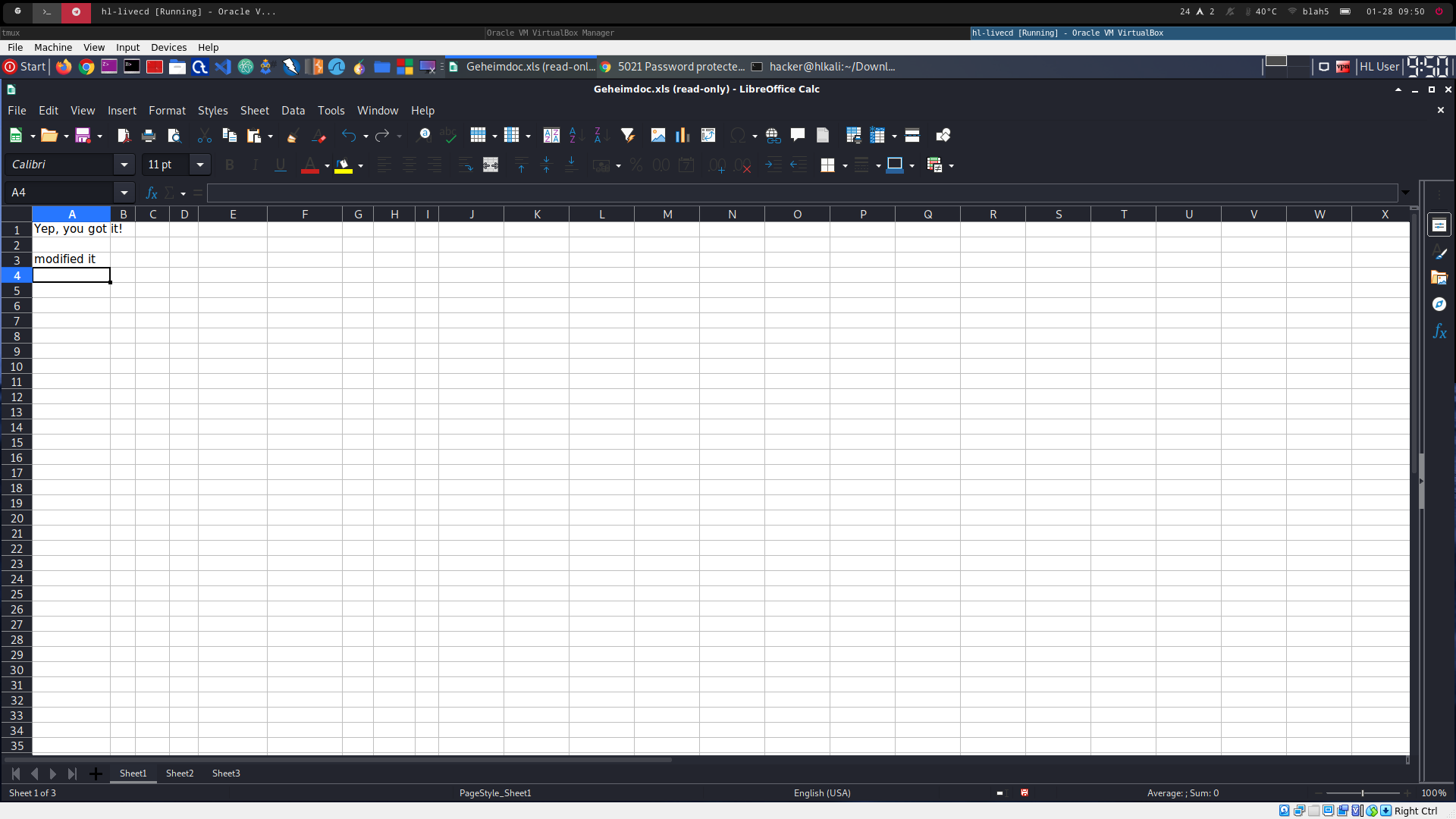
-
use stronger hashing algorithms, like in newer versions of Excel


