-
retrieve the Volume Serial Number:
fsstat usb_stick.dd
-
mount the image (readonly)
mount usb_stick.dd /mnt -o ro,loop,show_sys_files,streams_interface=windows
-
search for the file:
find . -regex '.*\.\(docx\|zip\)' (see 5101_1.png) -> not found
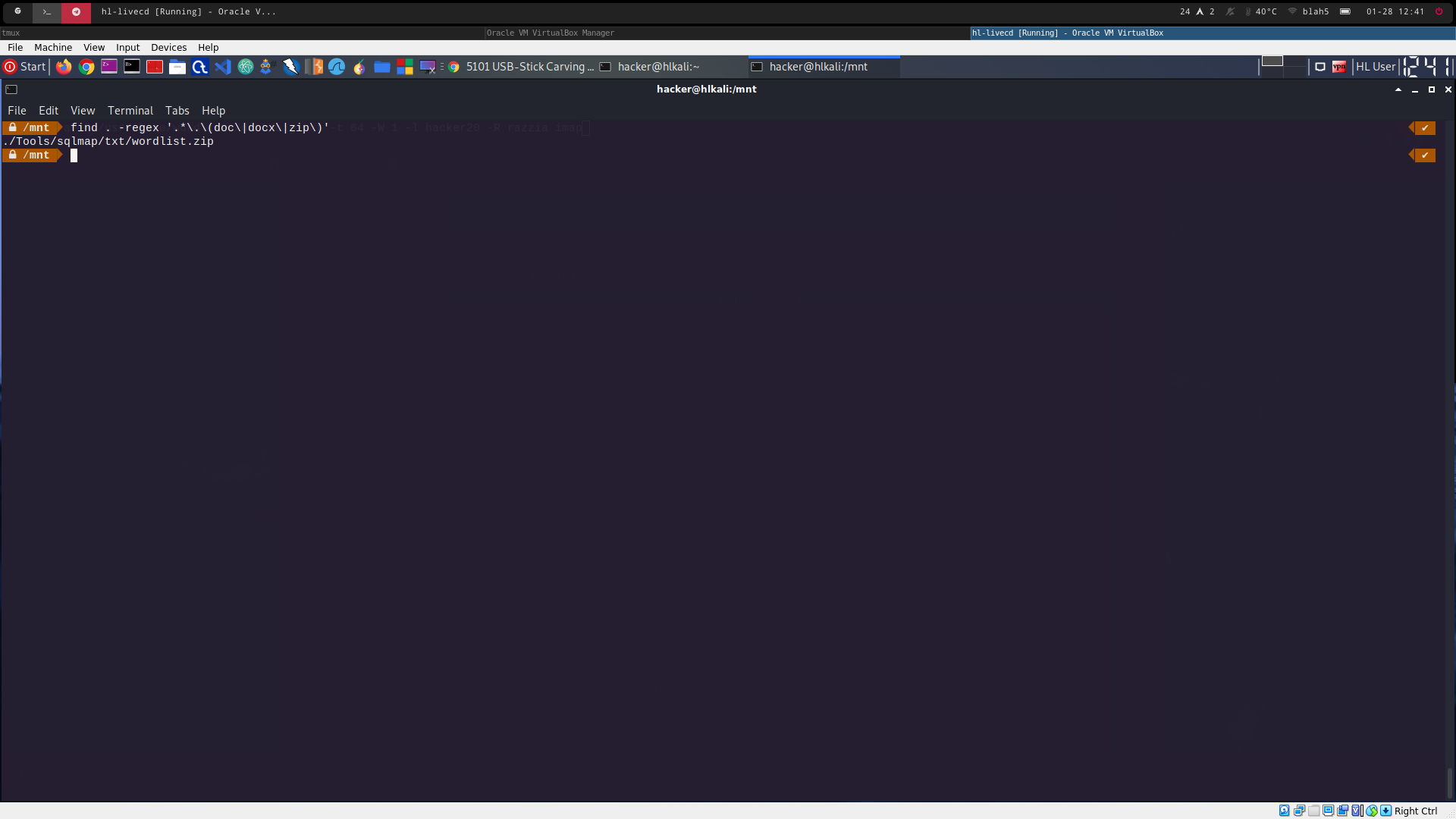
-
inspect the filesystem a bit more (docs, html, Tools, ZH)
-
the images in ZH appear to be normal images
-
the other folders contain information and tools to perform attacks
-
try to recover the file
-
the owner does not seems to be well served, so the file is probably still present on the stick, just not registered in the filesystem
-
foremost -t zip usb_stick.dd (filetype zip also includes docx files)
-
two zipfiles are found (see 5101_2.png)
-
00198696.zip: zip file containing a wordlist
-
00215144.zip: structure shows it's probably a docx file
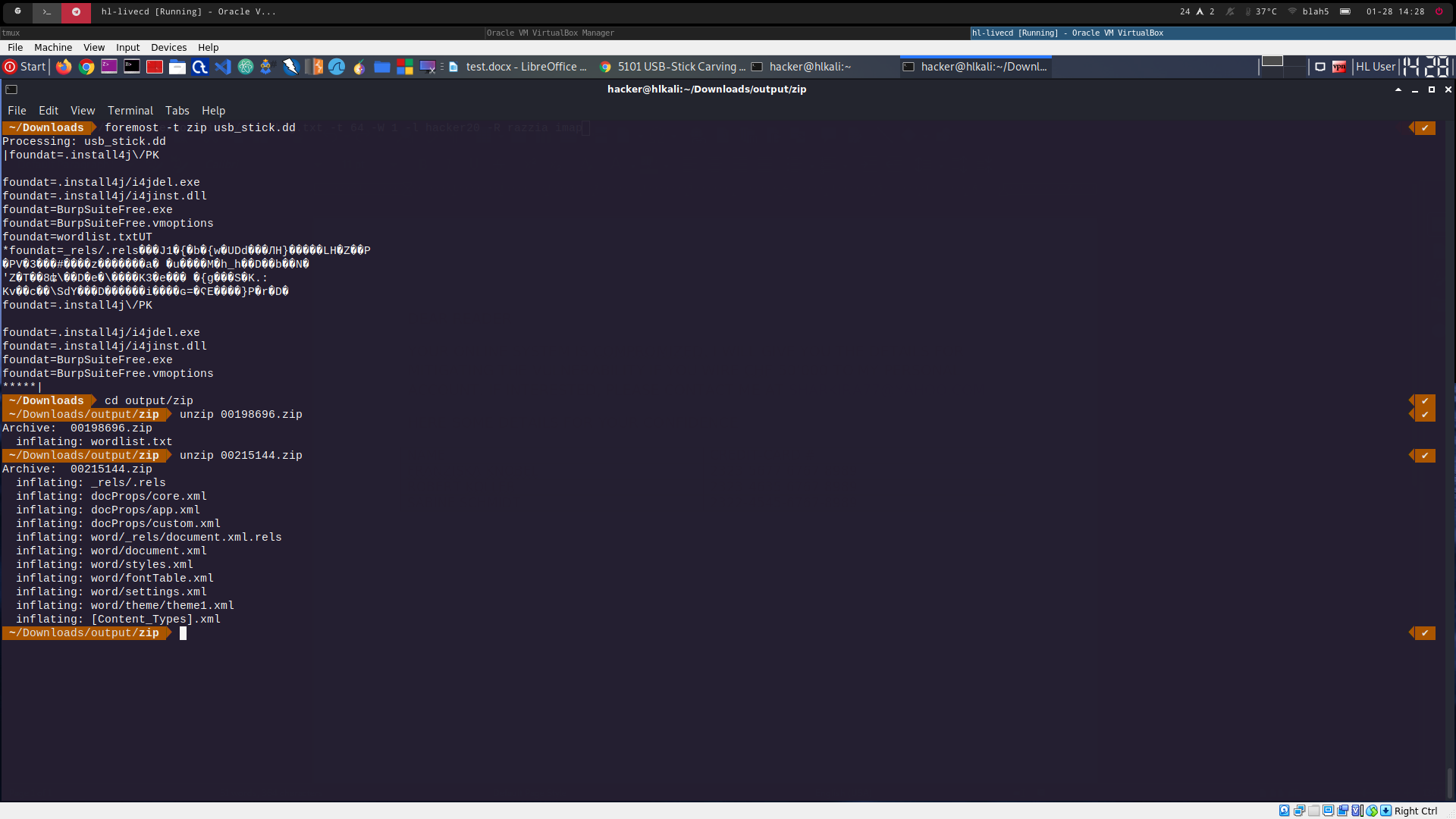
-
rename the indentified file to docx and open it with a reader
-
Volume Serial Number: AE78E78878E74DA1
-
the blackmail file was present on the stick
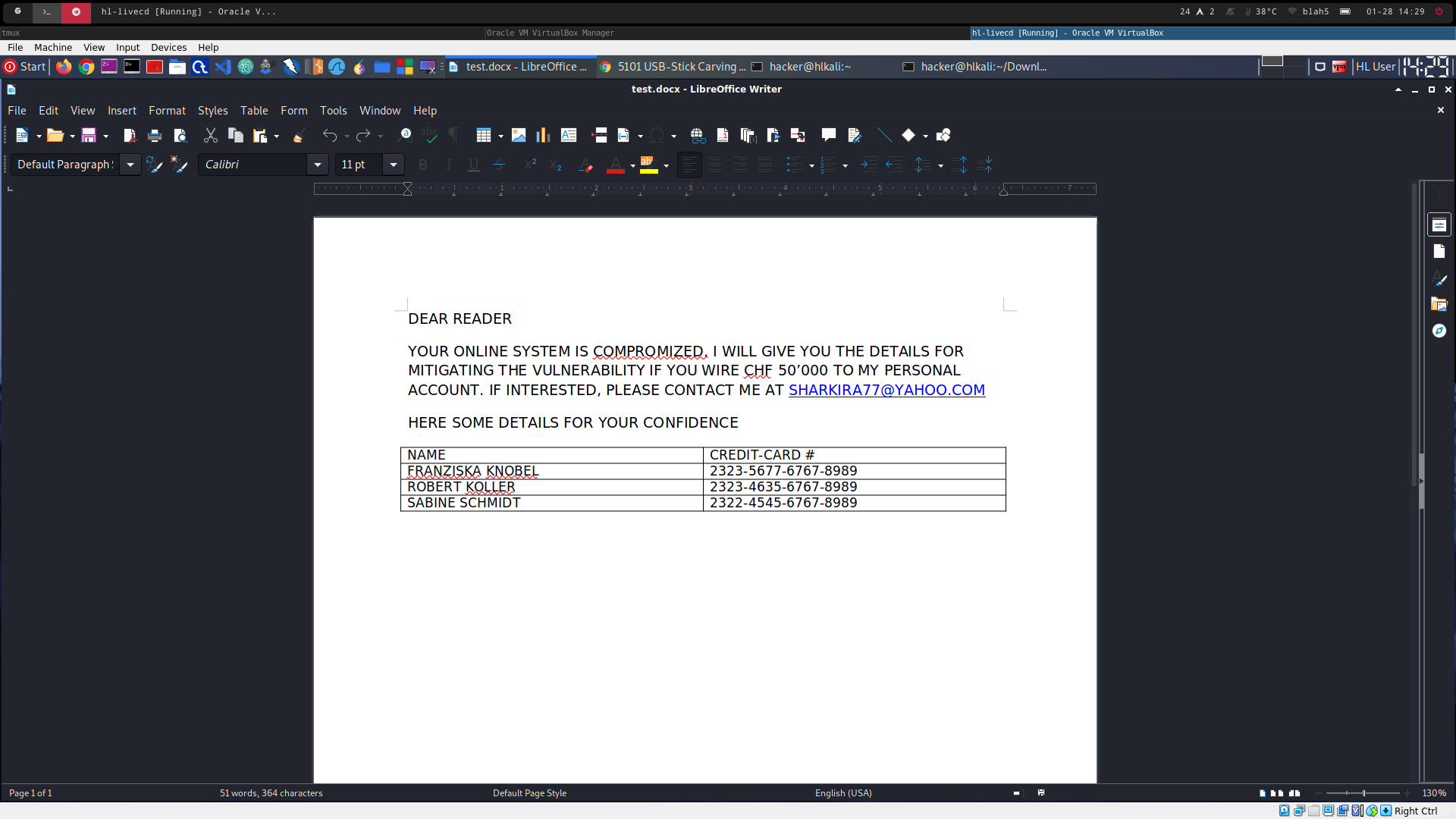
-
on the stick several tools to perform attacks and information about them are found, like sqlmap, burp



